When we started building our cloud encryption service, we knew it would be an uphill struggle to sell it. We just really wanted to build it – to show that encryption protecting your encryption keys from hosting provider can be done in a way suitable for the cloud.
I have recently dug out our initial specification – we called it “Project Nikka” then. We have defined five main features we wanted to provide – this is a direct quotation from the first page of that document:
- High-speed cryptography suitable for use in data-centers.
- Scalability with a fully automatic distribution of keys to an arbitrary number of devices. Transactions are processed regardless of the geographical locations of users.
- Controlled use of customer secrets (keys) – customer has control over its keys through physical tokens. Removal of such tokens will destroy all copies of the secrets (keys) .
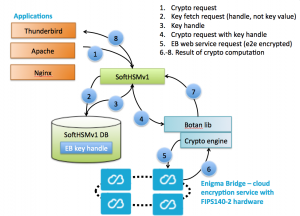
- Protection of customer secrets – customer keys are stored and used only in trusted and secure hardware – FIPS 140-2 Level 3 certified hardware.
- Detailed billing information about the use of particular secrets/keys per transaction.
We also had a comparison table to show what was available on the market (at the end of this post, if interested).
“Build then Fund” v “Fund then Build”
I don’t like to ask for money on the back of my thinking only – I always want to show something tangible first.
We’re pretty proud of what we’ve built. The question is, how to show that what we have is a proper piece of technology, not just “slide-ware”. I didn’t think about the problem in these terms, but one quickly realizes this is what it’s about.
We went to a few Fintech events. A major UK bank was present at one of them with their Startup Accelerator. We did have a nice conversation with a pretty girl, but she couldn’t understand what it is we do. She expected a mobile phone app, something she can install on her iPhone and play with it a couple of minutes later. It finally dawned on me that pitching an app is a much more economical. You can test a new idea twice a month with a skeleton app demonstrating the goal.
I Admire
However difficult it is for us, I keep admiring guys who believed they could beat Zilog, Motorola, and later on Intel and design much better (faster and energy efficient) processors – yes, I mean Acorn and spun-off ARM. Unlike Sinclair building clever and cheap computers, Acorn decided to build technically superior computers. It must have been hard to justify some decisions from the financial point of view, but the effort put into “building better things” must be admired.
There’s a BBC film called “Micromen” (a YouTube link) about Cambridge (UK) in the 80ies and Sinclair v Acorn – two big computer companies. Acorn was unimpressed with processors available at the time and decided to create their own processors (Project A in the picture).
While the processors had an immediate customer (Acorn computers themselves), and Apple later on, they did experience several hard set-backs but persevered.
We are lucky to be in Cambridge with many examples of a success. It was my absolute pleasure to work with Rick Dickinson, who did product design for my previous company.
Rick was behind the design of the Sinclair’s ZX-81 computer – a revolutionary design for a computer at the time. His Flicker photo galleries also show design sketches of planned gaming consoles.
We were also lucky enough to be listened to by Nicko and Alex van Someren, and other big names behind nCipher (now Thales-security) – technologists as well as sales guys. Guys with great experience in building encryption hardware and services in general. I could keep going …
… and you know what, I do feel better now again. So let’s get some work done 🙂
Initial Comparison to Market Leaders
We compared ourselves to crypto appliances – hardware security modules (HSMs):
| Existing HSMs |
Project Nikka | |
| Pricing | Per device | Use of device or per device |
| Speed – signing | 6,000 signatures | 50,000-100,000 signatures |
| Speed – encryption | 100MBps (fast processor) | 1.2 – 2,5 GBps |
| Key distribution | Manual – HSM owner | Fully automatic |
| Key deletion | Manual – HSM owner | Fully automatic – removal of physical token |
| Billing for use | Not supported | Per transaction |
A few years down the line, we have succeeded in almost all aspects. The main compromise was on speed – due to us being self-funded. The current production hardware is smaller than we envisaged, but it’s absolutely scalable. If you want 10x the performance, you just stack 10 boards in a server box. A reasonable compromise from the business point of view.



