We looked at 27 CT logs, which we have been processing and this note covers two aspects:
- frequency of updates – how long would your new certificate take to appear in CT logs;
- growth of the logs – how many items are being added to each of the logs to get a feeling for the dynamics of the ecosystem.
The following data has been collected over 6 weeks and the charts use ten measurements collected during that period.
Frequency of Updates of CT Logs
Although CT logs should provide a quick information about new certificates, not all the logs are updated with the same frequency.
As you can see in the table below, the variations are huge – from real-time updates of the Google CT logs called “argon”, to 6 hours update frequency of Symantec logs.
| ct.googleapis.com/aviator | closed | no new entries |
| ctlog-gen2.api.venafi.com | closed | no new entries |
| ctserver.cnnic.cn | closed | no new entries |
| ct.cloudflare.com/logs/nimbus2018 ct.cloudflare.com/logs/nimbus2019 ct.cloudflare.com/logs/nimbus2020 ct.cloudflare.com/logs/nimbus2021 |
60 mins | |
| ct.googleapis.com/icarus ct.googleapis.com/pilot ct.googleapis.com/rocketeer ct.googleapis.com/skydiver |
60 mins | possibly 5 minutes on either side of the interval |
| ct.googleapis.com/logs/argon2018 ct.googleapis.com/logs/argon2019 ct.googleapis.com/logs/argon2020 ct.googleapis.com/logs/argon2021 |
real time | less than 30 seconds |
| ct.ws.symantec.com sirius.ws.symantec.com vega.ws.symantec.com |
6 hours | |
| ct1.digicert-ct.com/log ct2.digicert-ct.com/log |
60 mins | |
| mammoth.ct.comodo.com sabre.ct.comodo.com |
10 mins | |
| yeti2018.ct.digicert.com/log yeti2019.ct.digicert.com/log yeti2020.ct.digicert.com/log yeti2021.ct.digicert.com/log yeti2022.ct.digicert.com/log |
60 mins |
Growth of Logs
The next thing I wondered was whether the big CT logs are quicker or the other way round. So let’s start with how each of the CT logs grows.
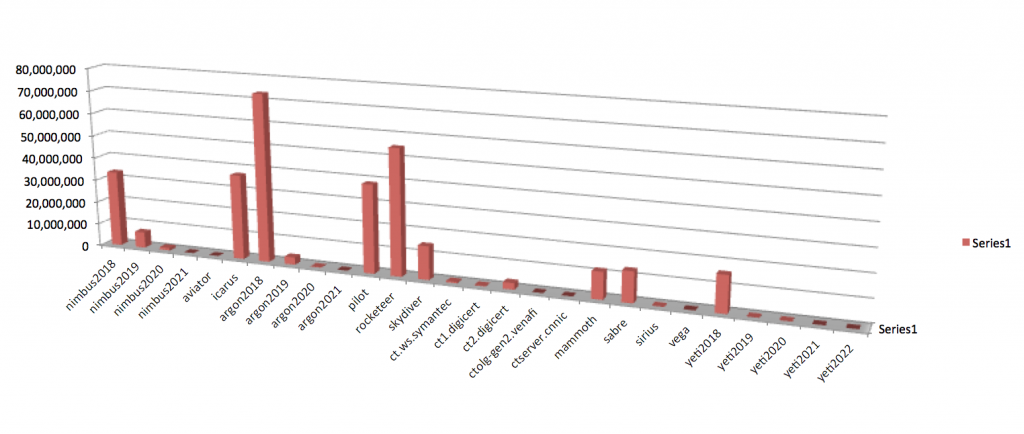
As you can see there are a few logs that grow significantly faster than others. Rocketeer and Pilot are among the biggest CT logs with over 410 million and 360 million entries respectively. Argon2018, Icarus and Nimbus2018 also have over 200 million entries.
The next chart suggests that the relative growth of CT logs has somewhat changed over the 6 week period so while snapshot figures give us a good indication, they don’t tell the whole story.
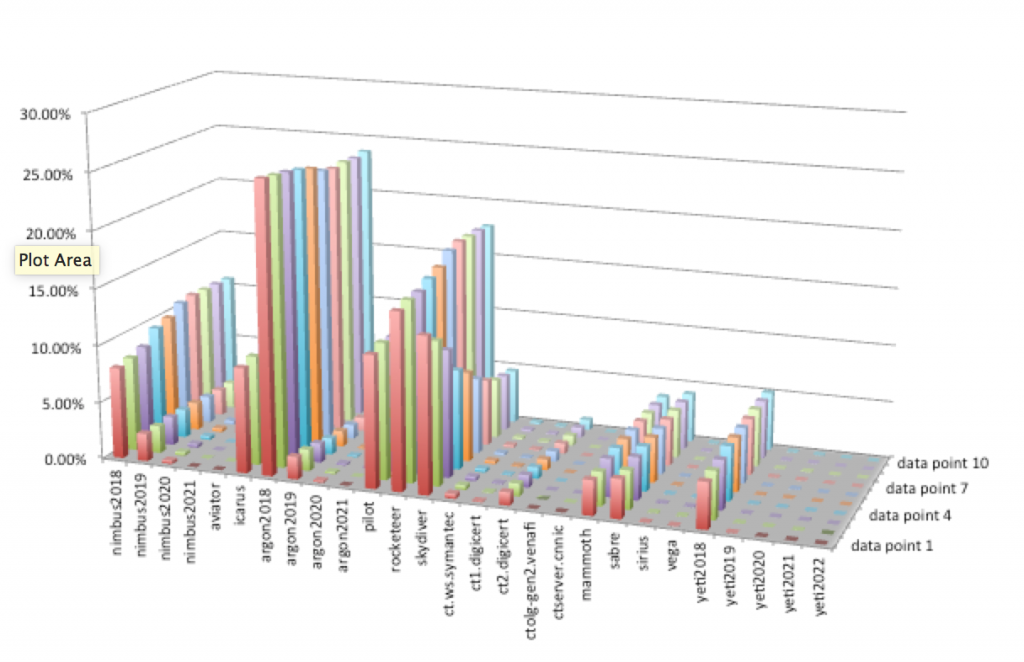
So where does it leave us. If you’re worried about attacks and unauthorized certificates and their exploitation for cyber attacks, you may want to find out which CT logs are used by your certificate issuer.
It also suggests that a quick notification system has its value to minimize any additional latency in discovering potential attacks against your internet services.
Why we’re looking into it?
We need a good source of information for real-time notifications for our KeyChest.net users. A new version is coming soon and we have built our own lookup table (currently with 6,600,000,000 rows) so we can provide you with the best possible analytics.