The WINES Infrastructure project deployed wireless sensor networks to monitor large bridges (Humber bridge), tunnels (London Underground), and water systems. Our task in the project was to perform a detailed analysis of security issues in existing hardware and software platforms for wireless sensor networks.
We chose not to concentrate on physical attacks as an attacker with physical access to motes could, with comparable effort, stage much more destructive attacks on the structure (bridge, tunnel) itself. We have implemented and tested several different attacks:
- data payload attacks that change the content of data packets;
- network attacks that affect the functionality of the network, for example by preventing communication, taking down specific links, modifying the routing topology or rewriting the firmware of a node; and
- system attacks, potentially the most damaging, in which the attacker exploits a vulnerability in one part of the system architecture (e.g. a wireless network) to gain control over other parts (e.g. a gateway or a data processing system).
The attack mechanisms used included jamming (at various degrees of selectivity and at different layers in the stack), re-play attacks, packet injection or corruption (where the injected or malformed packets were specifically crafted to probe for vulnerabilities or to trigger known vulnerabilities) and ACK spoofing. We measured effects of attacks by comparing the energy required for an attack to the energy used (wasted) as a direct effect of the attack.
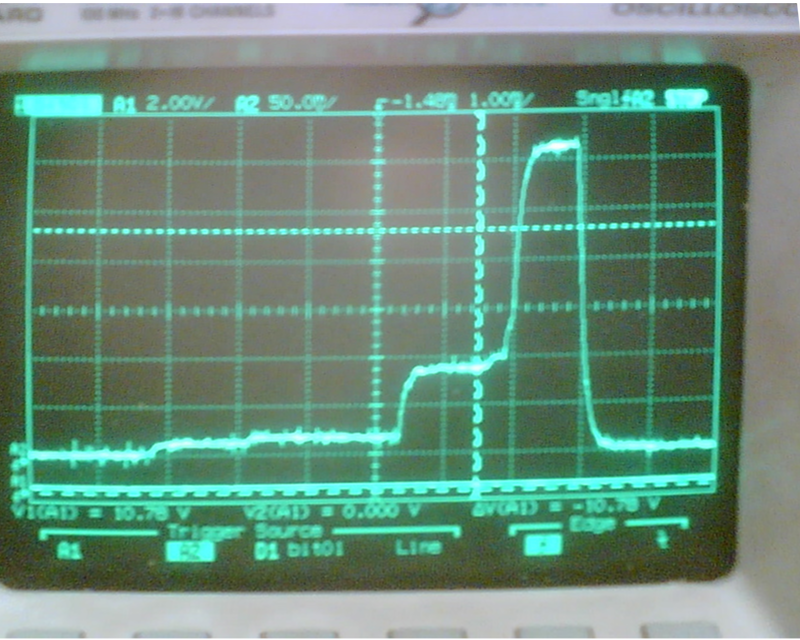
We used the practical experience from the implementation of attacks and information obtained from organisations managing large civil structures to create taxonomy of attacks and their significance for safety and security of civil structures.
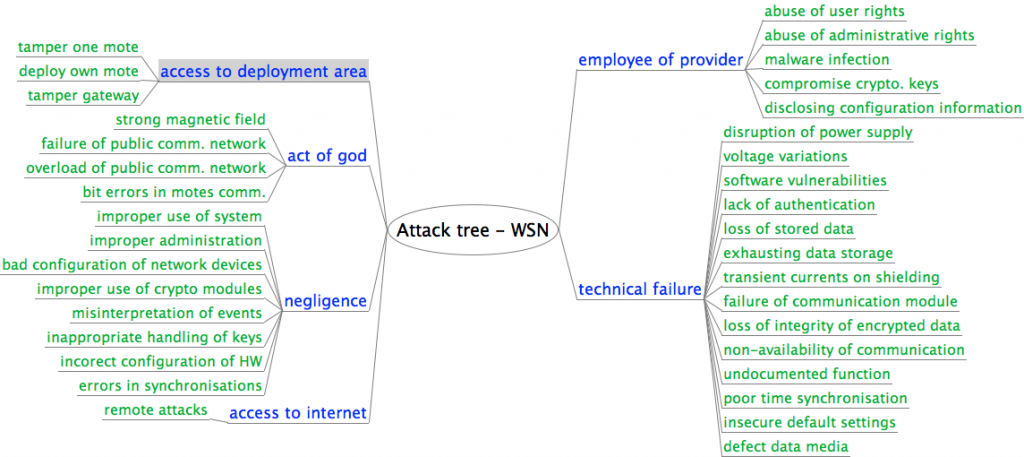
Description of our attacks and their implementations can be found in our paper Steel, Cast Iron and Concrete: Security Engineering for Real World Wireless Sensor Networks.
Among our other attacks, the most significant for the security researcher is probably our sleep deprivation torture attack based on routing table manipulation (section 4.5): it is crippling and very efficient because the attacker can set it up and walk away, as opposed to having to keep talking to the victims to drain their batteries out. Our selective jamming (section 4.3), too, is of interest as it is undetectable by OS and applications and can be used as the basis for more sophisticated attacks including packet rewriting (often assumed possible but rarely demonstrated in a modern ad-hoc radio context) and man-in-the-middle.
An extract from Conclusions