While implementing features of the certificate planner, we have added a few handy features to the KeyChest spot checker as well. It is now much more than just a tool to check when a website certificate expires.
 Initially, we thought that certificate time validity checks would be handy on their own. Well, once you build the “infrastructure”, it’s hard not to add more things, especially when developers are curious.
Initially, we thought that certificate time validity checks would be handy on their own. Well, once you build the “infrastructure”, it’s hard not to add more things, especially when developers are curious.
You can try it at https://keychest.net now, it is and will stay free.
Firstly, you can test any service using TLS. We have been testing web and email servers, but also our Spring web applications. As it’s a spot check, it should work for the laziest of us — real hackers. I’m trying to tell the guys here that they could automatically detect a simple paste and trigger searching straight away. Well, it’s on the to-do list, but other than that, you just copy a link from your browser and it should work. If not shout back!
If you add a port, the checker will use that port so it’s quite easy to test email servers, custom apps, and non-standard ports.
Server and CT checks
Once you get the checker going, it will have a look at several places:
- directly on your server and will try to do a TLS handshake; and
- certificate transparency (CT) logs, which contain (hopefully) all legitimate issued certificates that cause your browser show a green or gray padlock.
If there’s a problem, you will see it.
Thorough check-up
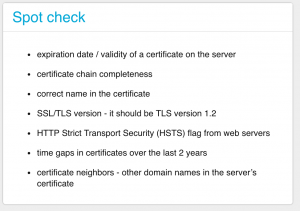
At this moment, the checker has collected quite a lot of data and will use it for some additional checks:
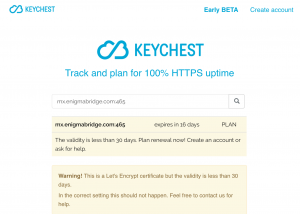
- time validity — there are three possible warning messages you can see: PLAN (if
Ferarri Centre with neighbors the expiration is in less than 28 days), WARNING (if the expiration is in less than 2 days), or ERROR (you’re down).
- chain trust — if there’s a certificate missing in the chain, e.g. when you don’t provide the root certificate, you will see a warning.
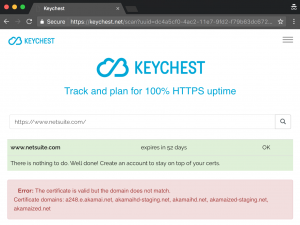
- hostname v certificate DN check — similarly, if the name in the certificate is not correct for the server.
- TLS version — you’re strongly encouraged to use TLS version 1.2 and the checker will tell you if it’s anything worse than that.
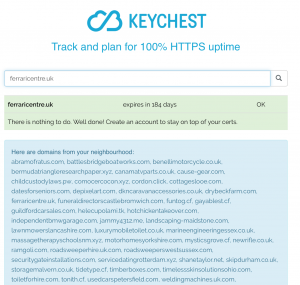
- multi-domain certs and wildcards (aka neighbors 🙂 — I wrote a blog post about CDN services, which save on certificates by grouping a number of them (up to 50) into a single certificate. You kind of get digital neighbors with the same SSL key. If this is the case for your server, the checker will show the neighbors. You can be a Ferrari centre, but your “neighbors” may include road sweepers welding machines, or luxury toilets 🙂
- downtime in 2 years — using purely data from CT logs, we can compute if there were any time periods when your server didn’t have any valid certificate. You can see a downtime warning of it’s the case.
- HSTS — if you’re really good, you have added an HSTS header to your web server. The KeyChest spot checker will notice that. Well done!
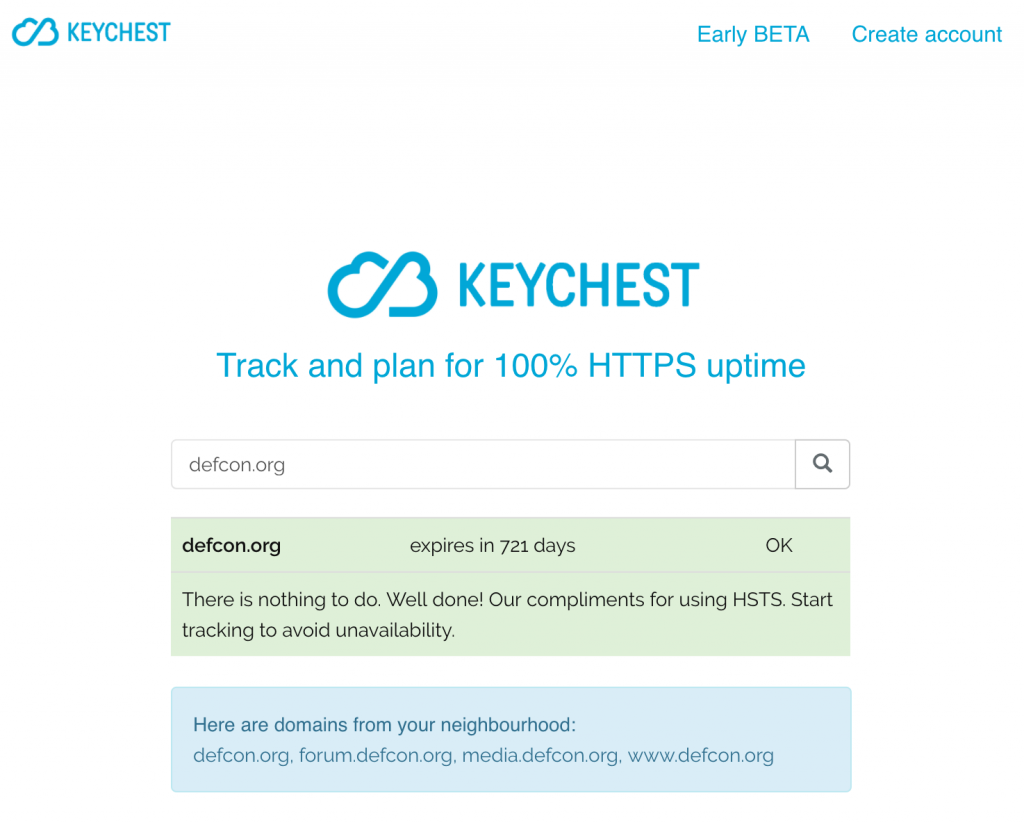
If all is good, you will only see a satisfying green “Well done” message. If there’s any problem (from the above) with your server, the checker will spit it out. That’s it — easy, quick.
… where’s the address bar … ok , copy … paste … bugger, expires in 23 hours! Have to go, see you later. 😉