Mandating use of HTTPS / SSL certainly seems to have something in common with security certifications like FIPS140-2 or Common Criteria. Very few understand how it really helps, how complex it is but many already know how costly it can be.
Enterprises have large teams (SecOps) who look after their encryption keys so that encryption doesn’t hinder the business. It is not unusual to have an annual budget of many millions of dollars just for this task. And it is neither unusual for this budget to be significant in the overall operational budget CISOs work with.
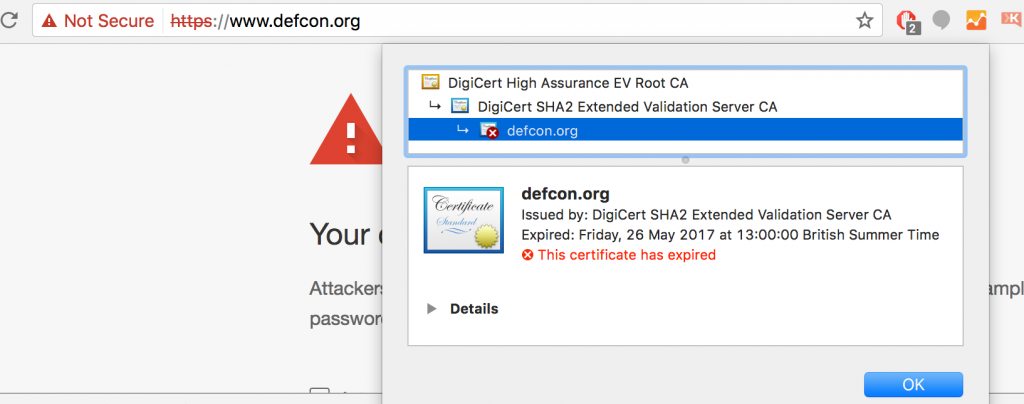
Small and medium businesses (SMBs) have been pushed towards adopting SSL in the last five years by tech giants who started showing good old HTTP websites as “Untrusted”. In fact, you can’t open a webpage without encryption on iOS (iPhone, iPad, iTV, …) devices at all.
The same “push and shove” comes from search engines, that penalize HTTP only websites as well. The result is clear – every small business with a web presence has to start using SSL.
Wikipedia has a good page about HTTPS, but even that has just one short paragraph explaining what is HTTPS actually good for:
HTTPS creates a secure channel over an insecure network. This ensures reasonable protection from eavesdroppers and man-in-the-middle attacks, provided that adequate cipher suites are used and that the server certificate is verified and trusted.
Now, correct me if I’m wrong, but the vast majority of web content is designed to be public. There are genuine good reasons to use encryption, but is HTTPS really the right approach?
Real-World SSL
The fact that there is no real, easy to understand security justification for using SSL, many companies just try to get it done. 99% of them will not really care much about the security of SSL, how the keys are stored, generated, how many people has access to them, nor whether they are misused. What they need is HTTPS, green padlock, to keep their business running.
Paradoxically, the real effect of that is creation of new business risks! Misuse of “security” is worse than not using any. The encryption will change the expectations of your users, clients, customers and they may become victims of malicious attacks more easily.
My Vision
KEYCHEST, a service I started two years ago as a free service has a simple vision that is stems from my beliefs, understanding of the security and me experience from SMBs, tier 1 banks, enterprises, and academia.
Make encryption an easy to use, commodity technology just like databases, networking, graphic interface.
Just because Google, Apple, Microsoft (vendors of web browsers) decided that using encryption is the right thing, we should not be left to pay for it. Automation is not the answer to everything but we can help with the “hard bits” – communication with certificate issuers, creating the files you need to install so that every administrator can do it easily without learning how things work.
Complexity of SSL
A not-for-profit company called Let’s Encrypt started giving out free encryption keys in 2016. They are free at the point of purchase but the “cost of ownership” can be very high, very unexpectedly.
The main problem is that these free keys (and certificates) have to be renewed at least 4 times a year (and the recommended use makes this 6 times a year). This can be automated, but here’s the snag. There are way too many moving parts involved in any renewal.
- There is Let’s Encrypt – they operate
- registration authorities (RA);
- certification authorities (CA);
- OCSP responders; and
- HSMs – protecting their high-value keys.
- Third-parties – operating certificate transparency (CT) logs where CAs have to successfully submit new certificates to may your browser accept them.
- DNS registrar – in some case you will need to update your DNS records.
- ISP – automatic validation will use IPv6 by default if there is a valid DNS record. If your ISP, cloud provider, or you can’t route IPv6, renewals will fail.
- Your web server needs HTTP port open – if you close port 80 (the bad, insecure HTTP), renewals will fail.
- Yourself / team – they need to make sure that new certificates are not only installed but also applied, e.g., web servers have to be restarted.
These are just the main items and the picture gets even more complicated when we start looking into the details of each of the items on the list.
Dan is the founder of KeyChest.net – AI (actual intelligence) Service for Network Encryption Control.