This post is about our application of a research I blogged about earlier – Investigating The Origins of RSA Public Keys.
You can also visit: https://enigmabridge.com/https.html .
The main purpose of https – ‘s’ denoting ‘secure’ – is to create a trusted connection for sending sensitive data between your browser and a web service. This is achieved by providing a secure digital ID of the web service (public key certificate). Until now, it has been widely accepted that such a digital ID didn’t contain any sensitive information that would endanger the security of the web service. No one expected that it could leak internal information about security management – information about methods, tools, and processes were supposed to be completely hidden from users as well as attackers.
The worrying discovery, made by Enigma Bridge co-founder Petr Svenda PhD, was awarded the best paper at the USENIX Security Symposium. It shows that sensitive information behind “https”, “tls” and other protocols can be extracted with sophisticated analysis using only information that every web service presents to anyone accessing it. Svenda and his team applied novel techniques to analyse millions of https keys and revealed how the keys were generated.
“I am puzzled with peeps are not all over this – enormous implications.”, tweeted Daniel Bilar, Information Security Specialist at Visa.
“It is striking that despite 30 years of cryptographic research, no-one has noticed this problem before. It has been hiding in plain sight all along.” Commented Professor of Security Engineering, Ross Anderson, after Svenda’s presentation at the University of Cambridge.
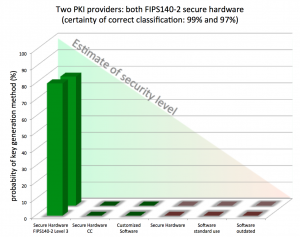
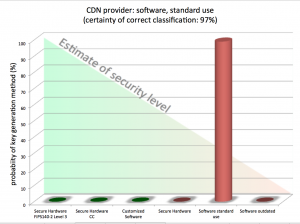
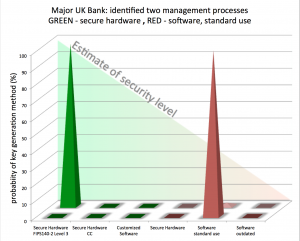
We have progressed the scanning methods to pinpoint how organisations, including blue chip companies, government departments or other companies, which are part of critical infrastructures manage their encryption keys using only publicly available information and identify potential weaknesses in their defences.
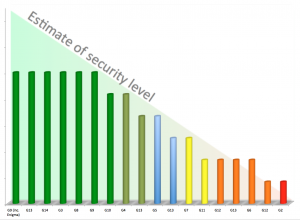
You can get a quick insight whether companies think about the quality of their encryption keys or let their administrators use any tool at hand – instead of using secure hardware key generators. Sharing keys between different applications is another aspect that suggests insufficient controls or enforcement of cyber security processes.
Whilst this vulnerability doesn’t compromise any web site directly, it demonstrates that even public information can leak security details and lead attackers to the most vulnerable targets. Use of validated secure hardware for key generation is the best approach to protect against many attacks. To help solve this serious issue, Enigma Bridge is proud to have developed a cost-effective, ground-breaking hardware security service which is based in the cloud.
One thought on “Your HTTPS Certificate Shows Where Its Key Comes From”