Self-driving cars demonstrate how integration of simple devices can build a sophisticated, autonomous system. Self-driving cars can see what is happening in their vicinity (“What’s around me”) and where they are heading (“Where Am I”). All this data is cleaned, combined, processed so that the car knows what to do.
When a company starts using a cloud platform, it is similar to taking a car on a road trip. Suddenly, the safety of a garage is gone. The answer to “Where am I” or “What to do” is not straightforward any more. There are many simple products solving small problems but there is nothing that would turn them into autonomous cyber-security solutions. Cyber security is still at the “simple device phase”.
Unless you go with us! We have just launched a cloud PKI service for Amazon AWS – professional PKI system with secure hardware, up and running in under 20 minutes. Not bad for a bunch of guys with a dream to build cloud encryption hardware. Give us thumbs up!
Enigma Bridge is building solutions from simple security products tied together with our cloud encryption platform. The main goal is to turn simple but hard to manage products into self-driving solutions. Adding a new “What’s around me” capability, i.e., detection of cyber attacks, as well as human errors. Our business is to protect, control, and detect use of data regardless of where it is stored or processed. Our strategy is to encase security tools, products, and applications between a management layer on one side and a protection layer on the other side.
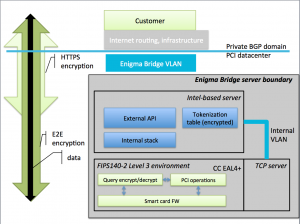
The protection layer – the Enigma Bridge platform – is where our core technology hides. Our scalable, cost-effective cloud-based encryption platform makes use of secure hardware to provide a trusted platform for monitoring, encryption, and audit of access to sensitive data.
The control layer is where we integrate a number of diverse tools and automate their deployment, use, and management using existing management platforms. The unique feature of our integration approach is the use of secure hardware. This gives customers ultimate protection of secrets and sensitive data that need to be stored and used centrally.
Centralized information management is unavoidable. Enigma Bridge minimizes the risk of a large-scale compromise. We reduce the number of centralized sensitive operations to the necessary minimum. We protect all sensitive data with a managed encryption service utilizing high-security hardware processors and near real-time monitoring of access to the sensitive data.
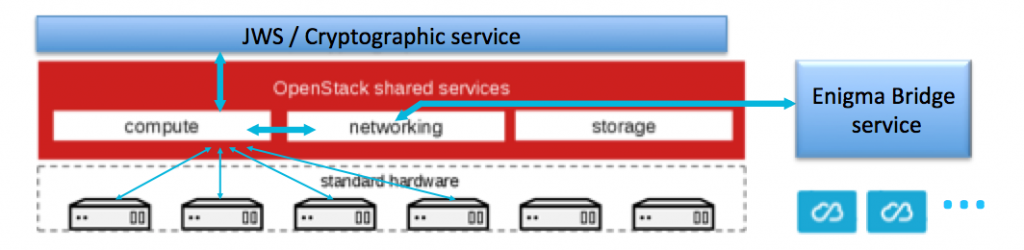
The Enigma Bridge platform is designed for cloud-use and it is delivered as: an API for integration into application logic, or as ready-to-use applications. We focus on applications for key management, whether it is in the public cloud and the internet, or internal networks.
One of our main targets is to make security as simple as possible and remove the need for security expertise in business development altogether. We have already implemented lightweight client libraries for several main implementation platforms.
The range of functions Enigma Bridge can offer includes database encryption, user authentication and protection of password database, protection of user PINs and card numbers in payment processing systems.
One may argue that using physical secure hardware is more than many applications need. If users can spot a difference between software and hardware encryption services, we believe there is no reason to favour one over another if users can’t spot the difference or when the high-security option is actually easier to use.