A month ago, we decided to launch EnigmaLink – our file-sharing application on ProductHunt. Neither of us used ProductHunt before, but I found a friend who could do the submission. I thought it would be straightforward.
Category Archives: enigmabridge
Hacking WiFi passwords – a randomness problem
Dusan, one of us @EnigmaBridge was curious about how are default WiFi router passwords generated and very quickly came up with an algorithm producing right passwords. And this “bootstrapping” problem is much bigger …
Continue reading Hacking WiFi passwords – a randomness problem
EnigmaLink on ProductHunt
I have mentioned EnigmaLink in my previous blog as our first application built on our cloud encryption platform (an easy to use alternative to CloudHSM from Amazon). Today, we posted it to the ProductHunt website.
“We created a cloud security platform.” – “so what?”
We have been working on a cloud security platform Enigma Bridge for the last couple of years. It was a great fun and … we built it. However, when we started talking to potential customers, we often had a hard time. We heard it was really interesting but what did it actually do?
Continue reading “We created a cloud security platform.” – “so what?”
A Long Dark Tea-Time of The Soul
You may know the mood when all seems to be done but new tiny issues keep cropping up every day … until they eventually disappear without you realizing it. The title has kind of sprung to my mind.
A lot has happened since my previous post and I indeed lived and breathed Enigma Bridge. While we kept focussing on a particular market segment we decided to make our products easier to test by smaller companies – a new test/staging instance of Enigma Bridge service will be launched within days. We did a good progress business-wise as well. But one thing I want to mention in particular is an ASIRTA tool – a baseline profiler for data governance. Continue reading A Long Dark Tea-Time of The Soul
Tokenisation – Introduction
Tokenisation is a hot topic as it makes card processing cheaper and more secure. The goal is to replace your card number with a random number that is hard to use for unauthorised transactions – and it removes the need to encrypt databases.
What we are primarily looking at now are mobile payments but we are designing solutions for e-commerce as well. Payment processing involves re-encryption of PINs (PIN-blocks) for card-present transactions.
The Importance of DNS to a Start-up
Our emails were not being delivered. I thought it was just my ignorance but a chat with a few more people around told me it was not the case. This is a story of a geek learning a (yet another) lesson the hard way.

Encryption for DNSSec
We have recently come across a nice check-list for whoever wants to use DNSSec and establish a good security baseline with a hardware security module (HSM), i.e., never get encryption keys compromised.
We will include detailed comparison of our platform to enigmabridge.com a little bit later but here is an initial comparison. Continue reading Encryption for DNSSec
Card Payments and The Cloud
We are now integrating encryption into a corporate infrastructure and it made me think about payments and PCI audits. PCI stands for Payment Card Industry. Anyone who got close enough to e-commerce, or card payments knows what a burden it is on running a business.
Sooo, I have spent some time this week thinking about architectures for “technical security systems”. I could say “cryptography” straight away, I guess. Thinking about protecting sensitive data that may be subject of independent audits.
The scope of PCI audits is given by storage and processing of credit card numbers and PINs (in case of Chip&PIN systems). Once you experience the pain, you definitely want to get “out of scope”. This is true for merchants just as banks.
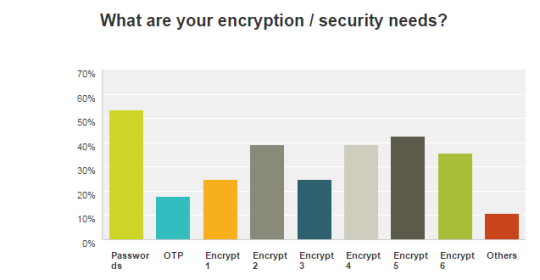
“One time passwords” are not passwords
We did a bit of research into what IT start-up companies need in terms of security. I did expect that secure authentication / logons would be at the top but I was surprised that OTP (one time passwords) were at the bottom.