KeyChest started as a simple HTTPS monitoring service. It has had its own database of all web certificates for about a year. And it helped issue first real certificates this week.
KeyChest’s business model is based on the management of HTTPS expiry. Automation of certificate issuance is for us an additional service that moves it closer to a complete service to manage your internal and external certificates. What it means in practical terms is that we simply pass on our cost of certificates to all paying users of KeyChest.
In terms of user experience, our primary goal was to make issuance of new certificates as simple as possible while preserving enough flexibility for the more technical users.
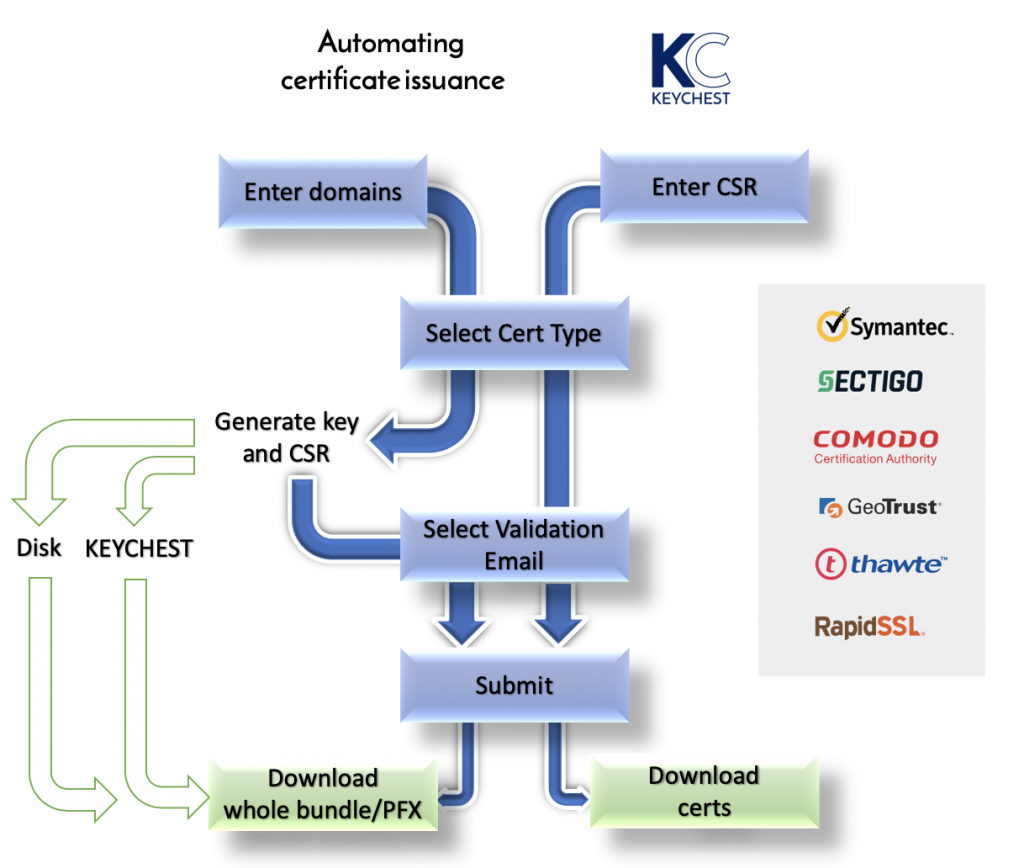
Let me start with the simple flow. The first step is to register a payment card. We need to pay issuers and so we need to charge you as well. This step will also add default values for the “company”, which are needed for certificate requests.
The actual certificate request starts with you entering one or more domain names. It can be single domains, or wildcard domains.
KeyChest will automatically select products that satisfy your domain names and calculate expected pricing. You simply select the most suitable product from this list.
We believe that email validation of requests is the preferred method wherever it’s possible. KeyChest will therefore obtain a list of allowed email addresses from a certificate issuer and you again simply select one from a list.
We are now ready to create the actual request. This happens completely in your browser. Once you enter a password to encrypt a new private key, KeyChest will generate a new key, create a request (PKCS#10 / CSR), and encrypts the secret part of the key with your password.
You can choose whether this secret key is stored on your disk or in the KeyChest database. Either way, a copy is stored in the local storage of your web browser. The request is then immediately sent out to initiate its validation by the issuer.
At this point, you need to complete required validation steps – in most cases this would involve following instructions sent via email. KeyChest will keep checking the request status and download the new certificate as soon as it is available. It will also send a notification if configured.
Voila – at this moment, you have all you need to install the new certificate on your server and KeyChest helps automating it.
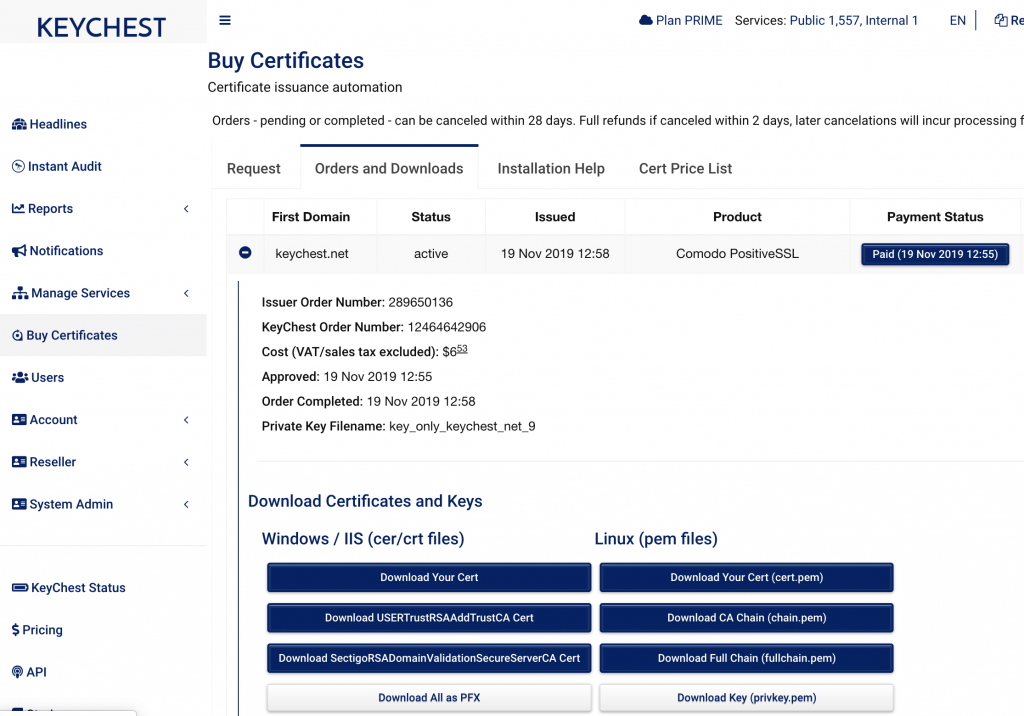
You can open your Orders and select the one you need. If your target server is an IIS, you click on “Download All as PFX”, enter a password to open the private key (if it’s still in your browser storage, it will be automatically found). Click the same button again and you get a password protected file you can import to IIS. It contains all the certificate and the key. The next step is simply to update the 443/https binding on your web site.
You can see that we avoid sending any secrets over the network. However, you may not want to copy your secret/private key away from where it should be used. Possibly, you already have a CSR file and want to use that instead.
If this is the case, you simply upload your CSR at the beginning of the certificate request. You don’t have to fill in domain names – they are in the CSR – and you can simply select the product and send the request to the issuer.
Once the new certificate is ready, you can download the certificate files and install them on your server.
Most domain-validated certificates will take a couple of minutes from entering a domain name to downloading a complete bundle for your server. The financial side is automated as well so you can download an invoice at the same time, if you need one.